What is a Robocall?
A robotic call (or “robocall”) is a telephonic communication instance in which a machine originates a voice call intended for a human being to answer. The machine in this case is a robocall technology platform consisting of hardware and software designed to automate call set-up in a manner in which a human being need not dial digits. Instead, a robocall computing platform auto-dials phone numbers.
Some robocalls are completely ethical and lawful, meaning that they are in compliance with applicable rules and regulations. An unlawful robocall is usually executed in a highly unethical and deceptive manner, typically using number spoofing in which the calling party’s phone number is altered electronically so it appears to be a number that is different than the actual originating party caller ID.
Number “Spoofing” is used by Bad Actors to Trick Called Parties
In other words, the calling number may look like it is coming from the United States, but it is actually being originated from some foreign country such as India. A specific form of spoofing commonly employed is “neighborhood spoofing”, which is altering a phone number so that it looks like a “neighbor” number (e.g. a number in the same NPA/NXX as the called party). This trick is used with the notion that a called party would be more apt to answer if it appears to be a number of someone they may know from their local area.
Bad actors engage in robocalling (as opposed to placing regular phone calls) for many reasons including the ability to achieve scale (many calls to many people very quickly) at a very low cost. One of the big reasons that bad actors place robocalls is that they can act with impunity. They do this by hiding behind technology firewalls (so to speak) to hide their true location and identity.
Robocalls vs. Regular Calls
Unlike regular, human-originated calls, bot-initiated calls do not involve a person waiting for the connection to occur (e.g. for someone to answer). Instead, the robocall platform itself waits for a connection, and upon the called party answering, a second connection is initiated to a human being on the other end of the call.
This occurs by employing Voice over Internet Protocol (VoIP) based communications. VoIP is very flexible, scalable, and inexpensive compared to traditional Time Division Multiplex (TDM), circuit-switched technology. This means that robocall platforms can place many calls very cheaply via VoIP than they ever could with TDM.
Robocall Technology Drivers
Robocalls have become a wide-scale problem largely because advancements in telecommunications and IT technologies have dramatically reduced telecom and computing infrastructure costs as well as expenses associated with placing bot-assisted phone calls.
Robocall platforms consist of hardware and software designed to place automated calls at great scale, meaning they can place many calls, to many people, very fast. Robocalls require little or no human involvement other than platform programming and implementation.
While robocall platforms may be located virtually anywhere, implementation of robocall platforms involves interconnection with public telecommunications networks so that robocalls may ultimately reach their intended recipient, a human end-user device such as a landline phone or smartphone on cellular networks.
Do Robocall Platforms make Random Calls?
While it’s conceivable that robocall platforms could call completely random numbers, they need telephone numbers recognizable as being part of the North American Numbering Plan (NANP) to be successfully routed over the public telecom network.
NANP numbers are recognized by the following format (NPA) (NXX) XXXX where the NPA is the area code, NXX is the phone number exchange (e.g. block of ten thousand numbers) prefix, and XXXX is a range of 10K numbers within the prefix.
As long as a given telephone number follows this NPA-NXX-XXXX convention, the public telecom network can route a call to a given number to successfully reach a person that is in control of that number (e.g. they have landline phone or cellphone).
However, some numbers are invalid (e.g. NPA/NXX combination was never assigned by numbering authorities), unallocated (e.g. it is a valid number, but never allocated from numbering authority to any communications service provider), or unassigned (e.g. it is a valid number, and assigned to a carrier, but not assigned or activated by a carrier). For example, a block of numbers is allocated to a carrier, but they have not yet set-up the number in infrastructure such as provisioning in a Home Location Register (HLR).
Therefore, robocall platforms could be programmed and configured to call completely random numbers, but they would not often reach an actual person. Instead, the goal of robocallers is to dial only valid phone numbers that have been allocated and assigned.
How do Robocalls Reach the Public Network?
A common question about robocalls is: Where do they come from and how do they get onto the public network? If it’s a machine calling me, how does it connect to the network in the first place?
Robocall platforms need to basic things to operate:
- Phone numbers to call
- Interconnection to the public telecom network
In the next two sections we discuss where robocallers get the phone numbers and how robocalling platforms interconnect to the public telecom network.
How Robocallers Acquire Phone Numbers
For most ethical, lawful robocallers, telephone numbers are provided to them on an opt-in basis from their constituents. For example, public schools require that the parents of students provide a home phone number and/or cellular numbers. This allows the school to reach parents in an emergency.
Bad Actors Do Not Follow the Rules to Acquire Phone Numbers
On the other hand unethical and/or unlawful robocallers acquire numbers without opt-in and often by nefarious processes such as purchasing or stealing number lists. However, they also have other means at their disposal other than stealing personal information. There are few potential mechanisms for how robocalling systems acquire numbers:
- Direct Targeting: Robocallers may target numbers directly (if they keep in their own database of numbers they may have purchased or acquired somehow). An example of a completely ethical, lawful, and opt-in manner in which this may happen is a school using a robocaller to alert parents of delayed start due to weather issues. An example of an unethical way in which this may happen is one’s name and number combination being acquired unbeknownst to them from the Internet or from their own phone such as via a smartphone app.
- Name ID Databases: Robocallers may access Name ID databases such as those maintained by various companies that provide premium caller ID services to display the name of the calling party along with the number. These are often referred to as Calling Name (CNAM) databases. Another source is something called the Line Information Database (LIDB). Some of these DB are operational in nature (like Toll Free Calling DB) and others are administrative. If the robocaller can get this information to use in their operation, they will know the name of the person they are calling.
- Calling All Numbers: In this variant, a robocaller uses all phone numbers from the universe of all known number ranges in the United States. Since it is a machine placing the call, the robocaller does not even care if they mistakenly dial a non-existent or disconnected number.
Like many databases, robocalling lists are thought to be actively managed, continually updated as they seek to reach a broad number of people and/or a certain demographic such as the elderly.
In terms of number selection from a database, the robocall platform can call numbers randomly or sequentially (as may be found in the phone book or other public directories).
Again, it is important to note that methods involving random or sequential calling in which the called party has no relationship with the caller are considered unethical and unlawful. This is especially the case in which the calling party has the intent to defraud the consumer.
How Robocallers Connect to the Public Telecom Network
Prior to placing a call, a robocall platform must first interconnect with the public telecommunications network. Robocalls rely upon Voice over Internet Protocol (VoIP) based facilities for interconnection between the robocall platform and public telecom switches as well as inter-system transport (e.g. carrying the call between networks and often over great distances).
How does a Robocall Work?
Regardless of how a robocalling system acquires a number, they place phone calls in the same three-step process, which is discussed in the following sections.
Robocall Technology Step 1: Placing Call to a Phone Number
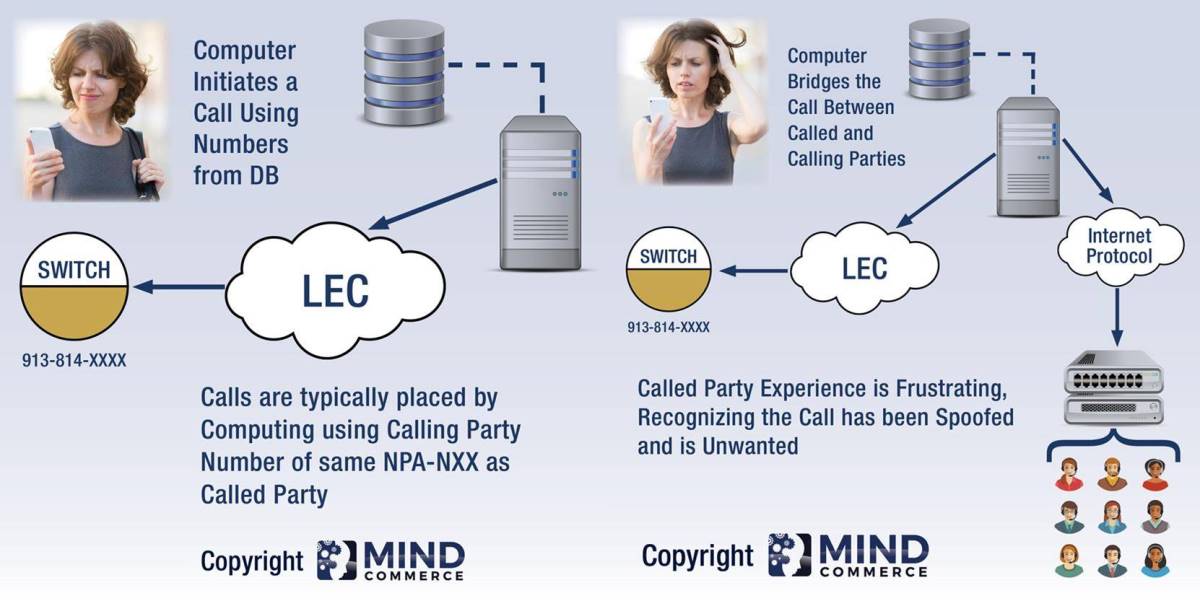
The first step of the robocall process is to place an initial call segment to an intended target phone number. For the sake of this example, the number chosen is in the NPA/NXX of 913/814.

In this diagram, the called party receives a call that appears to be someone in her own NPA/NXX, which in this case is some number of the form 913-814-XXXX. The machine placing the call chooses this with the intent of spoofing the real calling party entity and also to incentivize the called party to answer as she may think it is someone she knows.
A Robocall that Appears to be from the Same Area Code and Prefix as the Called Party is referred to as “Neighborhood Spoofing”
In some cases, people may not answer calls from unknown callers in which nothing appears in the calling party name field of their phone. In other cases, people will answer the call, thinking it may be someone they need to speak with that perhaps is simply not programmed into their phone with the associated name of the phone number.
What if the Called Party Does Not Answer?
In the case that the called party does not answer, the machine will terminate the call, typically leaving no voicemail message. Remember, it is a machine placing the call, so it only matters to the calling party that the called party answers.
This is because robocalls associated with Problematic callers (spammers, scammers, etc.) desire to reach a live person so they can pitch (a deal, a threat, a trick to steal money, etc.) in real-time over the phone.
In contrast, many lawful robocalls will actually leave a voicemail message, such as the school late start example mentioned earlier – they do want you to get the message.
What if the Called Party Does Answer?
In the case in which the call is answered by the called party, Step Two takes place in which the machine places a separate call. The machine waits for an audible acknowledgement on the called party side such as “Hello?” to recognize that it may proceed to step two: Robocall system places a separate call segment to a Call Center.
Robocall Technology Step 2: Separate Call Segment
In the second step, the machine places a separate call, typically to a call center, which is more often than not in some foreign country.

Completion of the separate call connection leads to the third and final step, which is the machine bridging the two call segments together.
The robocall system needs to bridge the two call segments together into one complete call between called party (number dialed by machine) and calling party (someone connected to the second call segment that is located in a call center).
Robocalls can be Placed from Anywhere on the Planet via VoIP
It is important to note that the second call segment does not need to be connected to a call center. It could in fact be connected to single phone or other device and/or a single person. The call center scenario is provided as a typical and illustrative but need not be the case.
Robocall Technology Step 3: Bridging Two Call Segments
In step three, the machine bridges the two call segments together. One portion of the call is from machine to called party. The other portion of the call is placed to some other location.

Even though the incoming call (from the called party’s perspective) appears to be originating from a number within the 913-814-XXXX range of numbers, it is really coming from a machine, which itself could be located anywhere.
What Appears to the Called Party as a Single Call is Actually Two Call Segments
As indicated earlier, the machine can bridge the call segment to virtually anywhere on the planet. While this bridging of the call segments (forming a complete connection end-to-end) happens relatively quickly, there is some delay.
This explains how there is sometimes a brief delay with a robocall as the called party waits for the second connection and bridging process.
Robocall Detection and Unwanted Call Mangement
In summary, a robocall is an instance in which a computer causes a call to be placed to a normal phone number. From the called party’s perspective it appears to be one call. However, the computing platform actually bridges two call segments together (one segment from platform to called party and another segment from platform to call center). It does this upon detecting an answer from the called party.
ICT is constant evolving. Switching and transport (data and voice) are continuously getting less expensive and easier to deploy. Convergence of computing and telecom is allowing an integrated approach to call completion, which when used ethically, has great benefits for society. The problem is that these and other robocall technology components are also being exploited by the unethical and unlawful.
Existing apps are available to assist consumers in terms of identifying robocalls and provide guidance to help a customer deal with potential unwanted calls. However, there is much work to be done in terms of identifying and stopping certain types of calls at the network level before they even reach the end-user.
Contact Mind Commerce to learn more about Robocall Detection and Unwanted Call Management Solutions.




Leave A Comment
You must be logged in to post a comment.